CVE-2023-33294: Execute Commands as Root from KaiOS 3.0 Browser via TCT Web Server
Vendor: KaiOS Technologies Inc.
Vendor URL: https://www.kaiostech.com/
Versions affected: KaiOS 3.0
Systems Affected: KaiOS-based mobile devices
Author: Tom Barrasso
CVE Identifier: CVE-2023-33294
Risk: Critical
Summary
KaiOS is a mobile operating system based on Firefox OS. KaiOS 3.0 comes shipped with a binary, tctweb_server, exposing a local web server that responds to HTTP requests on port 2929.
This server responds to GET and POST requests, accepting a application/x-www-form-urlencoded formatted request body with key-value tuples separated by '&', with a '='.
tctweb_server runs as root. It supports pre-defined commands for getting & setting system properties, reading & writing NV items, and reading files. It also allows for execution of user-provided bash commands.
Because the server is exposed on http://127.0.0.1:2929, and it returns the header Access-Control-Allow-Origin: * with every request, it is accessible to all installed apps and websites the system browser.
Location
- Source:
/system/bin/tctweb_server
Impact
Because tctweb_server runs as root, accepts arbitrary bash commands, and is accessible via the system browser, it has a very high potential for abuse.
This risk is partially mitigated by SELinux enforcement. As a result, tctweb_server cannot be used to read, write, or modify files or permissions within protected partitions.
The following are examples of what can be accomplished simply by visiting a malicious website on a KaiOS 3.0 device.
- Using
cmdshell=readfile to get the list of installed applications (system/b2g/webapps/webapps.json), or user profile data including notifications and downloads (folder: data/b2g/mozilla/*.default/, files: downloads.json, notifications.json)
- Modifying or deleting local files, i.e. in
sdcard/
- Bricking the device by enabling the kill switch system property
persist.moz.killswitch
An attacker can make XMLHttpRequest or fetch requests to http://127.0.0.1:2929 with parameters to run commands as root.
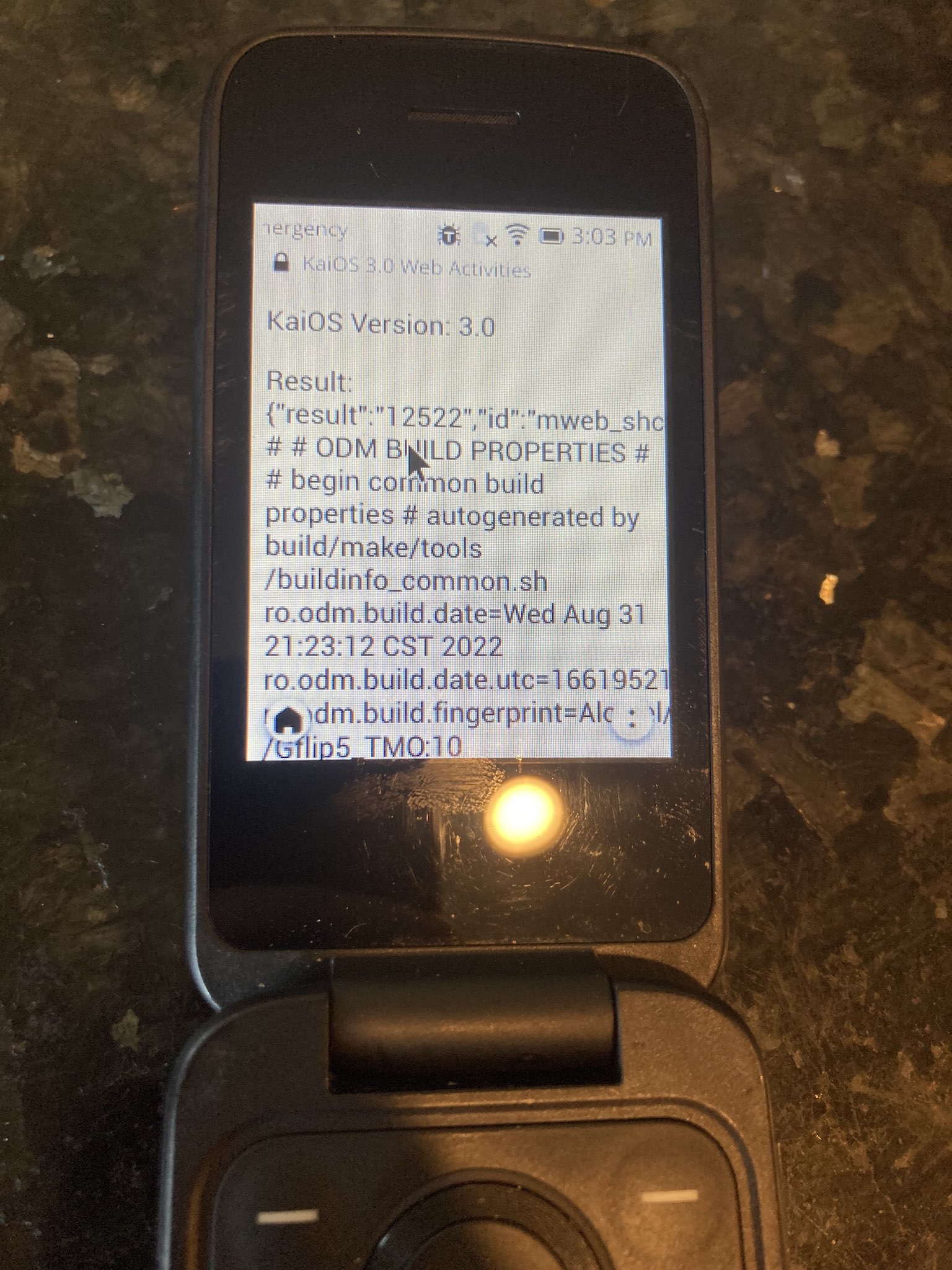
In this simple example, the contents of the build.prop file are displayed on screen.
let xhr = new XMLHttpRequest();
xhr.open('POST', 'http://127.0.0.1:2929', true);
xhr.send('cmd=bash&cmdshell=readfile&filename=system/build.prop');
Recommendation
Given the strong potential for abuse, the tctweb_server binary should either be permission-restricted to only certified apps or removed altogether. Analysis of builds from the Nokia 2780 Flip suggests that tctweb_server was removed in KaiOS 3.1.
Demo
This demo displays the contents of build.prop on screen.
KaiOS Version:
build.prop
Vendor Communication Timeline
- 5/2/23: Tom emailed [email protected] asking for PGP key used for secure communication.
- 5/5/23: Tom disclosed issues to KaiOS Technologies.
- 5/8/23: KaiOS Technologies acknowledged this issue.
- 5/15/23: Tom asked for the current remediation status.
