CVE-2023-27108 was published today, outlining a vulnerability in KaiOS 3.0 & 3.1 exposing call logs without user interaction to apps and websites.
Why it matters? KaiOS 3.0 & 3.1 users in the US may be inadvertently exposing their call log records simply by visiting a web page.
Background
KaiOS 3.0 was released in September 2021 with the Alcatel Go Flip 4 and TCL Flip Pro. It is the successor to KaiOS 2.5 and to date is only available in the United States. Although developers can publish applications for KaiOS 3.0, at the time of writing, no hardware device shipped with DevTools enabled nor have hackers gained root access. In November 2022, the Nokia 2780 Flip was released, and since it was SIM unlocked, KaiOS developers hoped that like prior Nokia devices, it would be developer-friendly.
@Farooq and @Affe Null of the KaiOS Discord were able to extract the system image from the Nokia 2780 Flip, WND (HWID 0). The system image includes the JavaScript that powers the Boot2Gecko system. Developers hoped this would lead to the discovery of secret debug codes. This was not the case, but in the process, other features and vulnerabilities were uncovered.
CVE-2023-27108: Technical details
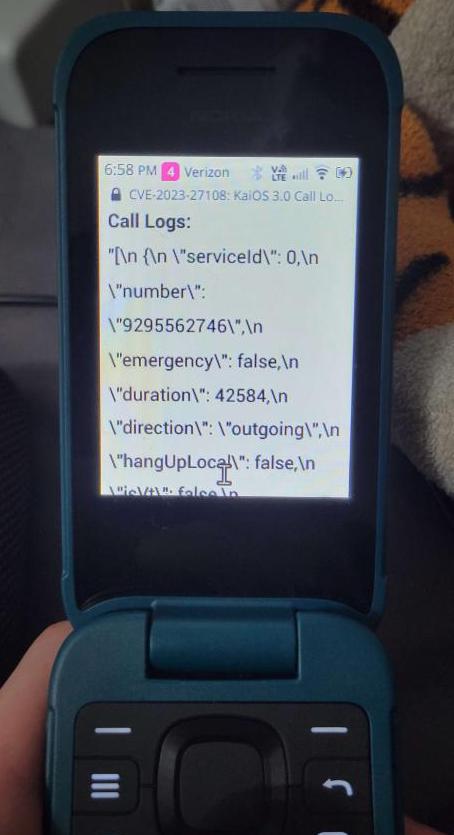
In February 2023, I discovered that the pre-installed system Communications app on KaiOS 3.0 (source: /system/b2g/webapps/communications/) declared in it’s manifest.webmanifest a
Web Activity for retrieving the user’s call logs.
1"getCallLogList": {
2 "filters": {
3 "type": {
4 "required": true,
5 "value": [
6 "calllog/tel"
7 ]
8 }
9 },
10 "returnValue": true
11}
In KaiOS 3.0, Web Activites are handled by Service Workers. Here is a simplified example of how this activity is handled within the serviceWorker.js script in the Communication app.
1self.onsystemmessage = (evt) => {
2 evt.waitUntil(
3 (() => {
4 switch (evt.name) {
5 case 'activity':
6 const handler = evt.data.webActivityRequestHandler();
7
8 if (handler.source.name === 'getCallLogList') {
9 db.getAllData()
10 .then(list => {
11 handler.postResult(list);
12 })
13 .catch(() => {
14 handler.postResult([]);
15 });
16 }
17
18 break;
19 })()
20 );
21};
The Service Worker calls the method getAllData from a wrapper class that returns the call log data stored in IndexedDB. Because there are no permission checks, nor is the allowedOrigins property set in manifest.webmanifest, call log data is returned to any caller. This means that any app or website you visit can access call log data without user interaction.
How It Works
Any app or website executing JavaScript can instantiate a WebActivity in KaiOS 3.0. The start method returns a Promise that resolves to an Array of objects containing call log data.
1let activity = new WebActivity("getCallLogList", {
2 type: "calllog/tel",
3});
4activity.start()
5 .then((callLogList) => {
6 // @param { String } number - tel number
7 // @param { String } date - call time
8 // @param { String } callType - call in/out/miss
9 // @param { String } duration
10 });
It’s this simplicity and lack of user interaction that makes this exploit especially dangerous. Simply using an app or visiting a web page is enough for a malicious actor to access your call logs, which can subsequently be sent to a remote server via XMLHttpRequest or fetch.
Recommended Mitigation
getCallLogList appears to be used by the System app to display a phone book to the user. The easiest solution would be to set the allowedOrigins property within the Communication app’s manifest.webmanifest file to only allow the System app to call this activity.
1"datastores-owned": {
2 "calllog": { }
3}
Additionally, these data are made available via the Data Store API. Rather than expose call logs via a Web Activity, they should be accessed using Data Stores which is only available within Certified apps. In the rare case of Certified apps uploaded to the KaiStore, KaiOS can check the datastores-access property in their manifest to confirm that they do not access call logs needlessly.
Is KaiOS Secure?
To date, KaiOS only has 6 published CVEs, plus this one. Compared to Android’s 5,121+ CVEs, it sounds like KaiOS is more secure, right? Well the answer is more complicated.
Android has been around since 2010, is shipped on tens of thousands of devices, and used by billions as smartphones, tablets, and car infotainment (Android Auto). KaiOS was first released in 2017 and is available on under 200 devices. Unfortunately, many KaiOS devices stop receiving over the air (OTA) updates, including security updates, just one year after release. While many budget Android OEMs offer similarly poor support, the Google Pixel devices now come with at least 5 years of security updates. Further up market, Apple sometimes provides critical security updates more than 10 years after initial release.
There is no single measure of digital security, and no easy way to compare security profiles across different systems. Due to limited app availability and platform restrictions, you are probably not accessing a bank account or sharing credit cards via a digital NFC wallet on KaiOS feature phones. Nonetheless, always consider privacy, security, and usability when purchasing a phone for daily use.